Privacy-preserving image sharing through self-sovereign identity
Here we describe the output of the first DECaDE-DLT Field Labs, a collaborative project between the DECaDE centre and industry partners that identifies a problem use case and explores potential solutions. In the first DECaDE-DLT Field Labs, we designed a proof-of-concept self-sovereign identity (SSI) system to support privacy-preserving image sharing: a way for content creators to assert rights over images while protecting their identity.
Our SSI system enables photographers to share images, assert their rights over images, and remain anonymous while doing so. It has several potential applications, for example, whistleblowers and activists who want to share images that expose wrongdoing or bring attention to a cause but fear repercussions if their identity is tied to the image. We step through our SSI solution below, and our work is summarised in the following video.
Self-sovereign identity
Self-sovereign identity (SSI) is a digital identity management system that enables users to control the management of their identity. Users can collect credentials from issuers and can use collected credentials to generate identity proofs that can be presented to verifiers (Fig. 1). In this way, SSI is a decentralised identity management system – it places control of identity data with the user. Additionally, SSI can support privacy-preserving identity management. Users can generate Identity proofs that prove aspects of the user’s identity to a verifier without revealing complete credentials.

Our use case
In the field labs, we explored SSI systems in the context of a photographer who collects credentials related to photographs and uses such credentials to claim a relationship with an image to a verifier, without revealing their identity. We developed a use case to support this.
Our use case considers the following entities and goals:
- Ruth: a photographer who wishes to manage her rights over images, without revealing her identity.
- Thoday: a credential issuer who issues credentials demonstrating that a person is a member of the Thoday photographer organisation.
- Cavendish: a credential issuer who issues credentials showing registration of an image.
- Franklin News: a news agency who wants to use photographers’ images if the photographer can demonstrate that they registered the image.
Through the fields labs, we demonstrate that an SSI system can be used to realise these goals.
Output of the field lab
We used the Hyperledger Aries toolkit to produce a proof-of-concept SSI system for our use case. Hyperledger Aries is an SSI toolkit that supports the minimal disclosure principle, which means that users can collect credentials and present identity proofs that need not reveal entire credentials, only the minimal data necessary to meet the purpose of the identity proof request (e.g., revealing that a person is over 18, rather than their full date of birth). The Hyperledger Aries toolkit is well-suited to our use case. We design a system in which Ruth can collect photographer/photograph credentials, and then prove that she has registered an image without revealing her identity.
Collecting photographer credentials
Ruth connects with Cavendish and collects a photographer credential in a simple and quick process. First, Ruth copies a QR code from Cavendish into her wallet (Fig. 2(a)). Her wallet automatically establishes a connection with Cavendish and navigates Ruth to a credential application form (Fig. 2(b)). Upon completion, Ruth submits the form, and her application is processed by Cavendish. A photographer credential is issued by Cavendish and is displayed in Ruth’s wallet (Fig. 2(c)).
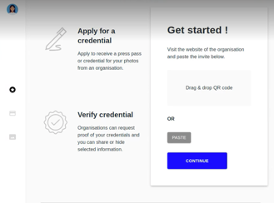
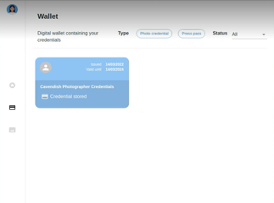

Figure 2. Ruth obtains a photographer credential from Cavendish.
From the perspective of Cavendish, their public portal (i.e., their website) displays the QR code used by Ruth, and credential applications appear in Cavendish’s private portal (Fig 3(a)). Cavendish performs offline checks to validate the information in Ruth’s application form and, if validation is successful, Cavendish issues the credential to Ruth (Fig. 3(b)).

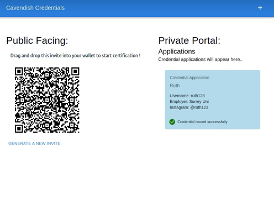
Figure 3. Cavendish issues a photographer credential to Ruth.
Collecting image credentials
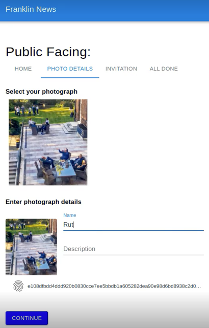
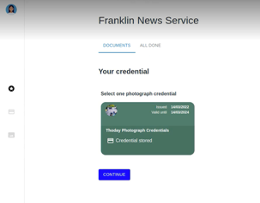
As a registered photographer, Ruth can now collect image credentials from Thoday. Ruth connects to Thoday and accesses Thoday’s credential application form by scanning the QR code on Thoday’s public facing site (i.e., like Ruth’s initial interaction with Cavendish). Thoday requires that Ruth is a registered photographer before issuing an image credential. As such, the application form directs Ruth to select her Cavendish photographer credential (Fig. 4(a)), which will be used to generate a proof of registration to Thoday. Ruth also uploads a photograph (Fig. 4(a)) and completes the application form by providing the image metadata (Fig. 4(b)). When Ruth completes the application, her wallet generates and displays a proof presentation for her Cavendish photographer credential (Fig. 4(c)). Thoday verifies her proof, and a credential is issued to Ruth. The credential is stored in Ruth’s wallet with a thumbnail of the photograph (Fig. 4(d)), which allows Ruth to quickly locate and use credentials for various images.
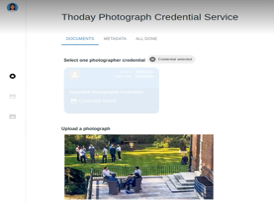
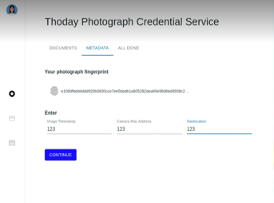
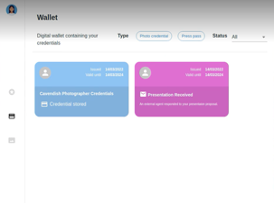
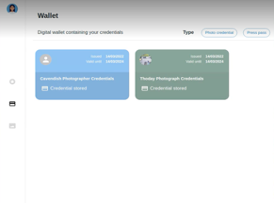
Figure 4. Ruth obtains an image credential from Thoday.
Thoday’s private portal displays Ruth’s credential application as a proof presentation (Fig. 5(a)). Thoday issues the credential (Fig. 5(b)) if the proof verifies successfully.
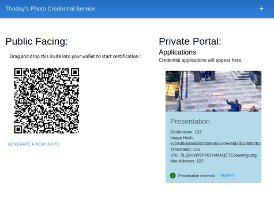
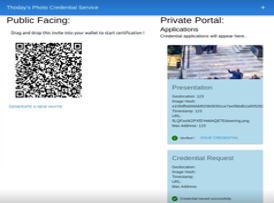
Figure 5. Thoday issues an image credential to Ruth.
Privacy-preserving image sharing
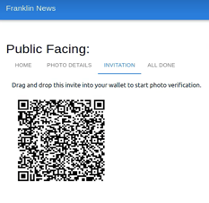
To share her images, Ruth can upload her image to Franklin News’ public website (Fig. 6(a)). Ruth will then be directed to prove that she has registered the image with a trusted (by Franklin News) image credential issuer (e.g., Thoday). To construct this proof, Franklin News’ website present a QR code that Ruth can drag and drop into her wallet (Fig. 6(b)). Ruth then selects the credential for the photograph she uploaded (Fig. 6(c)) and a presentation is generated by her wallet and submitted to Franklin News. Franklin News confirms to Ruth that her proof was successfully verified (Fig, 6(d)). Ruth’s presentation reveals only the hash of the photograph credential and does not reveal the metadata associated with the image or Ruth’s identity. In this way, Ruth has demonstrated her registration of the image without revealing her identity. By verifying the proof, Franklin News is satisfied that the (anonymous) photographer obtained a credential from a trusted issuer and is assured of the photographer’s rights to share the photograph.
Authors – Ashley Fraser and Steve Schneider
